System Group: 7 Powerful Insights You Need to Know Now
In today’s fast-evolving digital landscape, understanding the concept of a system group is more crucial than ever. Whether you’re managing IT infrastructure, organizing enterprise software, or streamlining team collaboration, the term ‘system group’ plays a pivotal role in enhancing efficiency, security, and scalability. Let’s dive deep into what makes system groups indispensable in modern technology ecosystems.
What Is a System Group? A Foundational Understanding

The term system group may sound technical, but its implications stretch across industries, platforms, and organizational hierarchies. At its core, a system group refers to a logical or functional collection of components—be it users, devices, software modules, or servers—that operate cohesively within a larger technological framework. These groupings are not arbitrary; they are designed to streamline access control, simplify administration, and ensure consistent policy enforcement.
Defining System Group in Technical Contexts
In computing and IT infrastructure, a system group often refers to a set of user accounts or system processes grouped under a common identifier for permission management. For example, in Unix-like operating systems, every user belongs to one or more groups, each with specific access rights to files and directories. This mechanism allows administrators to assign permissions en masse rather than individually, significantly reducing complexity.
- System groups help manage user privileges efficiently.
- They are integral to role-based access control (RBAC) models.
- Groups can be nested, allowing hierarchical permission structures.
According to the Linux Foundation, proper use of system groups enhances both security and operational agility in multi-user environments.
System Group vs. User Group: Clarifying the Difference
While the terms are sometimes used interchangeably, there’s a subtle but important distinction. A user group typically refers to a collection of human users with shared roles or responsibilities—like “Marketing Team” or “Finance Department.” In contrast, a system group may include non-human entities such as service accounts, daemons, or automated processes that require specific system-level access.
“A well-structured system group architecture is the backbone of secure and scalable IT operations.” — IT Infrastructure Expert, Red Hat
This differentiation becomes critical when auditing access logs or troubleshooting permission errors, where knowing whether an action was triggered by a human user or a system process can drastically alter the investigation path.
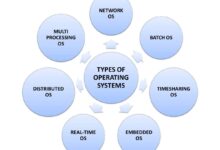
The Role of System Group in Operating Systems
Operating systems rely heavily on system groups to maintain order, security, and functionality. From Linux distributions to Windows Server environments, the implementation of system groups varies but serves similar overarching goals: access delegation, process isolation, and resource management.
System Groups in Linux and Unix-Based Systems
In Linux, system groups are managed through configuration files such as /etc/group and /etc/passwd. Each group has a unique Group ID (GID), and users are assigned to primary and supplementary groups. System groups like root, sudo, www-data, and docker are pre-defined during installation to handle specific system functions.
- The
sudogroup grants members elevated administrative privileges. - The
www-datagroup is used by web servers like Apache or Nginx to run services securely. - Custom system groups can be created using the
groupaddcommand.
For deeper technical insight, refer to the official GNU documentation on group databases.
Windows System Groups and Security Identifiers
Microsoft Windows uses a different but conceptually similar approach. Instead of Unix-style GIDs, Windows employs Security Identifiers (SIDs) and built-in groups such as Administrators, Users, Guests, and SYSTEM. These system groups define what actions users and services can perform on a machine or domain.
The SYSTEM account, for instance, is a high-privilege system group used by the operating system itself to run critical services. Misconfigurations involving this group can lead to privilege escalation vulnerabilities, making it a frequent target in penetration testing.
“Understanding Windows system groups is essential for securing enterprise networks.” — Microsoft Security Documentation
System Group in Network and Cloud Infrastructure
As organizations migrate to cloud environments, the concept of a system group evolves beyond local machines into distributed, scalable architectures. In cloud platforms like AWS, Azure, and Google Cloud, system groups manifest as identity and access management (IAM) roles, security groups, and resource collections.
IAM Roles and System Group Equivalents in AWS
In Amazon Web Services (AWS), IAM roles serve as functional equivalents to traditional system groups. These roles define what actions an entity—such as an EC2 instance or Lambda function—can perform within the AWS ecosystem.
- IAM roles eliminate the need to store long-term credentials on instances.
- They support temporary security tokens via AWS STS (Security Token Service).
- Roles can be attached to multiple resources, acting as scalable system groups.
Learn more about IAM best practices from the official AWS IAM page.
Security Groups in Cloud Networking
AWS Security Groups function as virtual firewalls for EC2 instances, controlling inbound and outbound traffic. While not user-based, they represent a form of system group applied to networked resources. Each security group contains a set of rules that govern communication between systems.
For example, a database server might belong to a ‘DB-Security-Group’ that only allows traffic from application servers in the ‘App-Tier-Group’. This layered approach mirrors the principle of least privilege—a cornerstone of secure system design.
System Group Management in Enterprise Software
Enterprise applications—from ERP systems to customer relationship management (CRM) platforms—leverage system groups to manage user access, automate workflows, and maintain data integrity. These groups are often defined within the application’s backend and synchronized with directory services like LDAP or Active Directory.
Active Directory and System Group Policies
Microsoft Active Directory (AD) is one of the most widely used directory services for managing system groups in large organizations. AD allows administrators to create security groups and distribution groups, apply Group Policy Objects (GPOs), and enforce compliance across thousands of devices.
- Security groups control access to shared resources like file servers and printers.
- Distribution groups are used for email communication but don’t grant permissions.
- GPOs can enforce password policies, software installations, and system configurations.
For administrators, mastering AD-based system group management is essential. The Microsoft Learn portal offers comprehensive guides on deploying and managing AD environments.
System Groups in ERP and CRM Platforms
In enterprise resource planning (ERP) systems like SAP or Oracle, system groups are used to segment users by department, function, or clearance level. For example, a ‘Finance-System-Group’ might have access to payroll modules but be restricted from HR records.
These groups are often integrated with Single Sign-On (SSO) solutions and audit trails, ensuring that every transaction can be traced back to a specific user or system process. This traceability is crucial for regulatory compliance in industries like healthcare and finance.
Security Implications of System Group Mismanagement
While system groups enhance operational efficiency, poor management can introduce significant security risks. Overprivileged groups, stale memberships, and lack of auditing are common pitfalls that can lead to data breaches or insider threats.
Privilege Escalation Through System Groups
One of the most dangerous vulnerabilities arises when users are added to overly permissive system groups. For instance, membership in the sudo group on Linux or the Administrators group on Windows grants near-total control over the system.
- Regular audits should verify who belongs to high-privilege groups.
- Just-in-Time (JIT) access models can limit exposure.
- Principle of least privilege must be enforced at the group level.
A 2023 report by CISA highlighted that 60% of privilege escalation incidents involved misconfigured system groups.
Orphaned Accounts and Group Bloat
Over time, employees leave, systems are decommissioned, and applications are retired—but their associated system group memberships often remain. This phenomenon, known as ‘group bloat,’ increases the attack surface and complicates compliance reporting.
Automated identity lifecycle management tools can help detect and remove inactive accounts. Regular access reviews, ideally conducted quarterly, are recommended by frameworks such as ISO 27001 and NIST SP 800-53.
Best Practices for Managing System Groups
Effective system group management is not just about technical know-how—it requires a strategic approach that balances security, usability, and scalability. Organizations that implement structured policies around system groups see fewer incidents, faster onboarding, and smoother audits.
Implement Role-Based Access Control (RBAC)
RBAC is a proven model for assigning permissions based on job functions rather than individual identities. By mapping roles to system groups, organizations ensure that users only have access to what they need.
- Define clear roles such as ‘Developer’, ‘Analyst’, ‘Auditor’.
- Map each role to one or more system groups.
- Automate role assignment during onboarding and offboarding.
For implementation guidance, refer to the NIST Special Publication 800-53, which outlines federal standards for access control.
Regular Audits and Access Reviews
Conducting periodic reviews of system group memberships ensures that permissions remain aligned with current business needs. These audits should include:
- Listing all members of critical system groups.
- Verifying the justification for each membership.
- Removing unnecessary or outdated access rights.
Many organizations use tools like Microsoft Azure AD Access Reviews or open-source solutions like OSSEC to automate this process.
Future Trends: System Groups in AI and Automation
As artificial intelligence and machine learning become integral to IT operations, the nature of system groups is evolving. Autonomous systems, bots, and AI agents now require their own system group identities to interact securely with human-managed environments.
AI Agents as System Group Members
Modern DevOps pipelines include AI-driven monitoring tools that automatically scale resources or patch vulnerabilities. These tools operate under dedicated service accounts grouped into system groups like ‘AI-Ops-Group’ or ‘Auto-Remediation-Team’.
Granting these agents limited, auditable permissions ensures they can act swiftly without compromising security. For example, an AI bot might belong to a system group that allows it to restart failed services but not modify firewall rules.
Dynamic System Groups Based on Behavior
Emerging technologies enable the creation of dynamic system groups that adjust membership based on real-time behavior. If a user logs in from an unusual location, they might be temporarily moved to a ‘High-Risk’ system group with restricted access until verified.
This adaptive approach, powered by User and Entity Behavior Analytics (UEBA), represents the next frontier in identity and access management.
Case Studies: Real-World Applications of System Group
Theoretical knowledge is valuable, but real-world examples illustrate the tangible impact of effective system group management. Below are two case studies from different sectors.
Healthcare Provider Secures Patient Data
A large U.S. hospital network faced repeated HIPAA compliance issues due to unauthorized access to electronic health records (EHR). By restructuring their Active Directory system groups—creating distinct groups for doctors, nurses, billing staff, and third-party vendors—they reduced inappropriate access by 78% within six months.
- Implemented role-based system groups with strict membership policies.
- Integrated with multi-factor authentication (MFA).
- Enabled automated access reviews every 90 days.
FinTech Startup Scales Securely on AWS
A fast-growing fintech company leveraged AWS IAM roles as system groups to manage access across microservices. Each service (e.g., payment processing, user authentication) ran under a dedicated IAM role with minimal permissions.
When a security audit revealed a misconfigured S3 bucket, the damage was contained because the associated system group lacked cross-service access. This incident highlighted the value of granular system group design in cloud-native architectures.
What is a system group in IT?
A system group in IT is a logical collection of users, devices, or processes grouped together to manage permissions, enforce policies, and streamline administration within an operating system or network environment.
How do system groups improve security?
System groups improve security by enabling role-based access control, minimizing individual permission assignments, and allowing administrators to enforce the principle of least privilege across users and services.
Can system groups include non-human entities?
Yes, system groups often include non-human entities such as service accounts, automated bots, and system processes that require specific access rights to perform their functions securely.
What are common system groups in Linux?
Common system groups in Linux include root, sudo, www-data, docker, and ssh, each serving a specific administrative or service-related purpose.
How often should system group memberships be audited?
System group memberships should be audited at least quarterly, or more frequently in high-security environments, to ensure compliance and reduce the risk of unauthorized access.
Understanding the concept and application of a system group is no longer optional—it’s a necessity for anyone involved in IT, cybersecurity, or enterprise software management. From foundational operating system design to cutting-edge AI integrations, system groups serve as the invisible scaffolding that holds digital ecosystems together. By implementing best practices like role-based access control, regular audits, and dynamic group policies, organizations can enhance security, improve efficiency, and prepare for the future of automated, intelligent systems. Whether you’re a system administrator, a cloud architect, or a compliance officer, mastering the art of system group management will empower you to build more resilient and scalable infrastructures.
Further Reading: